There have been some malware goofs in the past which are worth talking about. Ranging from the author’s identity being revealed to a decryption key being left on an encrypted machine and even some funny malware names. Let’s take a look at the three best malware fails of all time.
Inspired by the earlier Blaster.B (Blaster Worm) malware, 18-year old Jeffrey Lee Parson released a modified version of the Blaster.B malware which was designed to infect compromised computers with a backdoor Trojan. It’s worth noting that the original malware created a file called: “penis32.exe”, which can safely be said that the perpetrators were most likely of a young age.

Blaster.B (Blaster Worm) malware author Jeffrey Lee Parsons
The problem with what Jeffrey Lee Parson did was that he never covered his footsteps. The FBI came knocking on his doorstep almost immediately as the website that the malware contacted was registered using Parson’s real name and address, if that wasn’t bad enough the IP was traced back to his father’s internet provider. Parson was sentenced to 18 months in prison.
The “Hitler Ransomware” (Ransom.Hit) used a picture of Adolf Hitler stating the files on the system were encrypted. However it turns out that the files were not encrypted – presumably because this was out of the author’s range. What it did was remove the extensions from the files and to an untrained eye would appear if the files were indeed compromised. After an hour of ‘infection’, the malware would crash the system and after the user had restarted their system all the files were deleted. Deleted, not wiped – which means any disk recovery tool or undelete software could get the files back.
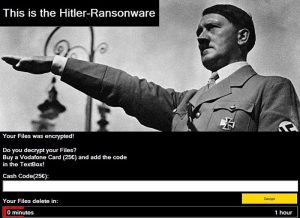
Hitler Ransomware (Ransom.Hit)
The Hitler ransomware also demanded €25 in pre-pay mobile credit as a ransom, anyone (if there was anyone) who paid the ransom wouldn’t have received a decryption key since there were no encrypted files to decrypt.
In 2012 the Remote Control Virus (Backdoor.Rabasheeta) got the attention of the public, more so in Japan. The malware hijacked computers and used them to issue threats. The author cunningly emailed a lawyer claiming to be the author and offering proof in the form of a ‘How To’ manual for the attacks. This proved to be a cat and mouse game for both the malware author and the authorities. By the end of 2012 the police were no nearer to catching the Remote Control Virus author and offered a reward of three million yen ($27,000) for information that would lead to an arrest. In January 2013, the attacker sent more emails to the media, this time containing a series of puzzles.

Remote Control Virus (Backdoor.Rabasheeta)
Solving the puzzles would provide the location of a cat. Bizarrely, the puzzles did indeed lead to a cat on the island of Enoshima. In the cat’s collar, the police found an SD card containing the malware’s source code. However, the malware author had slipped up. He didn’t realize there was CCTV in operation when he approached the cat. The footage allowed police to identify Yusuke Katayama, a 30-year-old Tokyo IT worker, who was subsequently jailed for eight years.
IntelliTeK is one of the fastest growing IT service providers in Australia. We are always up to date with the latest threats to emails and IT security which is why we only partner with the best in the industry. If your company isn’t fully equipped to fend off cyber criminals, then get in touch with us so we can discuss your options. Call us on 1300 768 779, email us at info@intellitek.com.au, fill out the web form, or have a Live Chat with us below.

