From file hacking to cryptocurrency stealing to school boy errors, here are three notable mobile ransomware which you should be cautious about.
SLocker
Largely imitating the Petya ransomware, SLocker combines with the use of the China-based social networking website QQ with its screen locking and file encrypting capabilities. It’s mission is to seize and lock your files. Upon payment they say they will decrypt and release the files. The most worrying thing about this ransomware is its ability to completely lock the screen of your phone, rendering it pretty useless.
This ransomware disguises itself as game guides, video players, and so on in order to lure users into installing it. When installed for the first time, the icon looks like a normal game guide or cheating tool. Once the ransomware runs, the app will change the icon and name, along with the wallpaper of the infected device.
Cerber
This ransomware has an unusual method of attack and that is to steal cryptocurrency. It targets three kinds of wallets – Bitcoin’s Core wallet and two third-party wallets from Electrum and Multibit. It also steals password information. Although this ransomware is unlikely going to cause mass destruction, it should still be treated as a significant threat. This method goes onto show that the ransomware authors are looking for ways to steal directly from the pockets of users and not by holding anything ransom from them.
Demon
The last out of the three appears to be an amateur effort into the world of ransomware because it doesn’t encrypt any files, it doesn’t steal any currency and it doesn’t even hijack any system or device whatsoever.
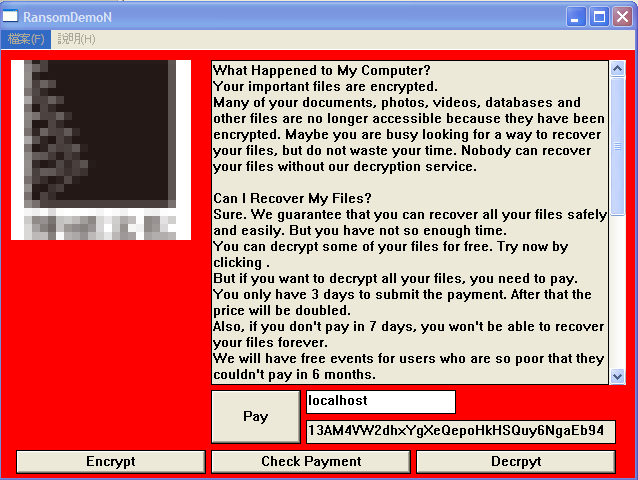
Demon ransomware
Looking at the above ransom note, the existence of an “Encrypt” button makes things seem a little unprofessional as nobody would want to encrypt their own files. The grammar of the text underlines that it originated abroad – the Chinese characters on the top left is the biggest giveaway. There is no direct threat to a user who receives this ransom note and perhaps it’s a bluff to get users to pay the ransom.
Most mobile ransomware infect devices via downloaded apps from the (Android) Google Play Store or third-party app stores. They originate from fake apps or attach themselves to legitimate apps and runs itself once the app has been installed on the device. By using these methods of infiltration, it makes it very difficult for antivirus software to detect the ransomware until it is too late.
About IntelliTeK Pty Ltd
IntelliTeK is a managed IT services company in Sydney, Australia. With major vendor relationships and accreditation’s from the worlds leading IT companies including WatchGuard, Microsoft, Trend Micro and Amazon Web Services, IntelliTeK have kept clients happy since 2007.
IntelliTeK are always up to date with the latest cloud backup solutions which is why we only partner with the best in the industry. If your company isn’t fully equipped to fend off cyber criminals, then get in touch with us so we can discuss your options. Call us on 1300 768 779, email us at info@intellitek.com.au, fill out the web form, or have a Live Chat with us below.

