Hackers use a vulnerability in popular web browsers such as Google Chrome, Mozilla Firefox and Opera to spoof the web address bar with ‘legitimate looking’ web addresses in order to steal login or financial credentials from users.
Millions of Internet users who are at risk of this sophisticated hard-to-detect phishing attack are recommended to disable Punycode support in their web browsers in order to temporarily mitigate this attack and identify such phishing domains. Us managed IT firms are aware of such a spoof attack but unfortunately we only really hear about it once it’s too late and the user has been a victim of an attack.
What this hack basically does is make it seem like you’re on a legitimate website, like PayPal for example, and upon entering your login details/financial details the data will go straight into the hands of cyber criminals. They do this is a very sophisticated manner – by replacing character(s) with unicode characters. The attack called, The Homograph attack, has been known since 2001 but browser vendors have struggled to fix the problem.
Many Unicode characters, which represents alphabets like Greek, Cyrillic, and Armenian in internationalised domain names, look the same as Latin letters to the casual eye but are treated differently by computers with the completely different web address. For example, Cyrillic “а” (U+0430) and Latin “a” (U+0041) both are treated different by browsers but are displayed “a” in the browser address.
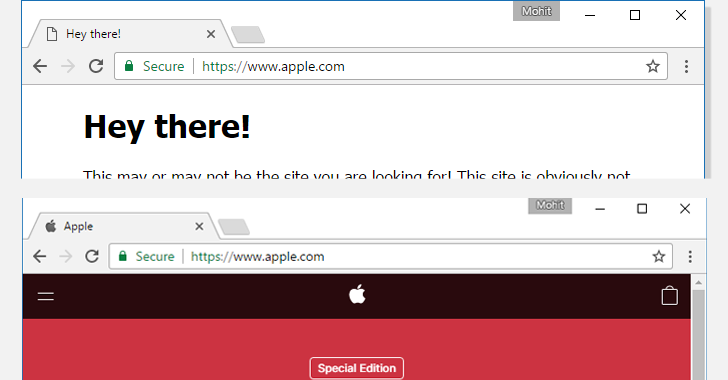
The loophole relies on the fact that if someone chooses all characters for a domain name from a single foreign language character set, resembling exactly same as the targeted domain, then browsers will render it in the same language, instead of Punycode format. This loophole allows a hacker to register a domain name like xn--80ak6aa92e.com and bypass protection, which appears as “apple.com” by all vulnerable web browsers, including Chrome, Firefox, and Opera, though Internet Explorer, Microsoft Edge, Apple Safari, Brave, and Vivaldi are not vulnerable.
While Mozilla is currently still discussing a fix, Google has already patched the vulnerability in its experimental Chrome Canary 59 and will come up with a permanent fix with the release of Chrome Stable 58, set to be launched later this month. Meanwhile, millions of Internet users who are at risk of this sophisticated hard-to-detect phishing attack are recommended to disable Punycode support in their web browsers in order to temporarily mitigate this attack and identify such phishing domains.
IntelliTeK Managed IT tips to prevent Homograph Phishing Attacks:
- For Firefox users:
- Type about:config in address bar and press enter.
- Type Punycode in the search bar.
- Browser settings will show parameter titled: network.IDN_show_punycode, double-click or right-click and select Toggle to change the value from false to True.
- Unfortunately, there is no similar setting available in Chrome or Opera to disable Punycode URL conversions manually, so Chrome users have to wait to get a patched Stable 58 release.
- Managed IT companies like IntelliTeK recommend good password managers which automatically enters your credentials on websites so that you don’t have to type them in over and over again, minimising the risk of having your credentials.
For all your other IT security concerns in and around Sydney, then get in touch with us so we can discuss your options. Call us on 1300 768 779, email us at info@intellitek.com.au, fill out the web form, or have a Live Chat with us below.

