Ransomware creators have a number of clever tricks up their sleeves to make sure that they go about their business unnoticed and make it difficult to undo their work. Let’s take a look at some of their methods.
Name Encryption
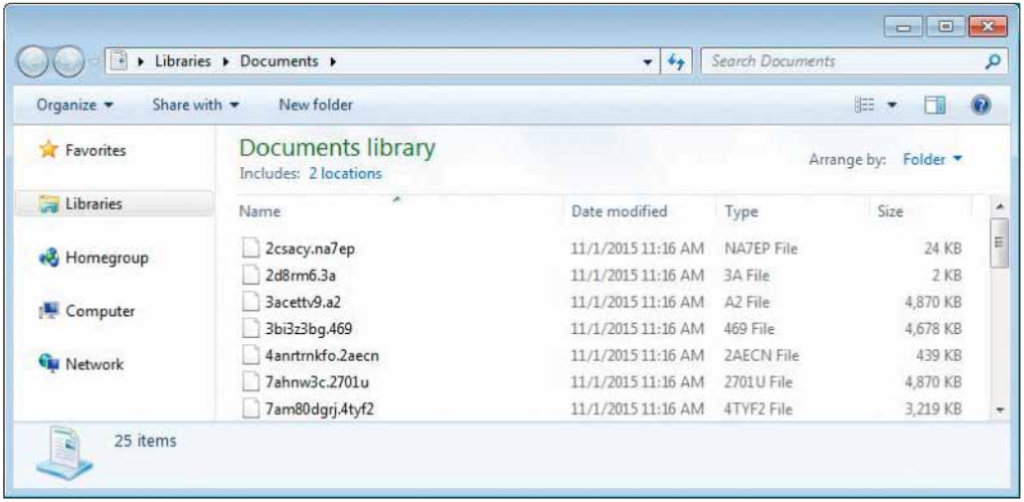
One of the more latest ransomware versions encrypt file names in the manner where it makes it near enough impossible to distinguish files from one another. The encrypted file names usually comprise of random letters and numbers:
Backup And Publish
Some versions of ransomware claim to have backup copies of data which are held on other servers and the cyber criminals make threats of publishing them online if the ransom is not met. There has been a number of stories suggesting that this method is indeed valid, with people and organisations having data scattered on the internet, available to anyone.
PCs, and Windows, and websites
Ransomware such as Linux.Encoder.1 will inject itself into websites with known vulnerabilities (such as shopping cart programs) and once on the host machine will encrypt all the files in the home directories and many of the directories referenced by typical websites (site images, scripts, code libraries, etc.).
Ransomware Predictions:
- Delayed ransom demands:
- Ransomware will encrypt in the background, so that backup and archive programs pick up the encrypted files and overwrite the backups. Once the encryption key expires, both the data and the backups will be held hostage.
- Hold the network hostage:
- Ransomware will use worm technologies to spread and remain dormant before initiating encryption, using networks, using shares, etc. Combined with a Stuxnet approach, an attacker could hijack an entire network.
- Encryption of the fly:
- Ransomware will use kernel components to hook the file system and encrypt files on the fly as they are accessed by the user to ensure maximum damage.
- Asymmetric encryption without the need for a centralized repository:
-
Ransomware authors realize that using a centralized repository for the encryption keys is a weak point in their strategy because it gives an attack point for security defenses. It is predicted that we will see asymmetric encryption that does not use a centralized repository.
-
If your company isn’t fully equipped to fend off cyber criminals, then get in touch with us so we can discuss your options. Call us on 1300 768 779, email us at info@intellitek.com.au, fill out the web form, or have a Live Chat with us below.

